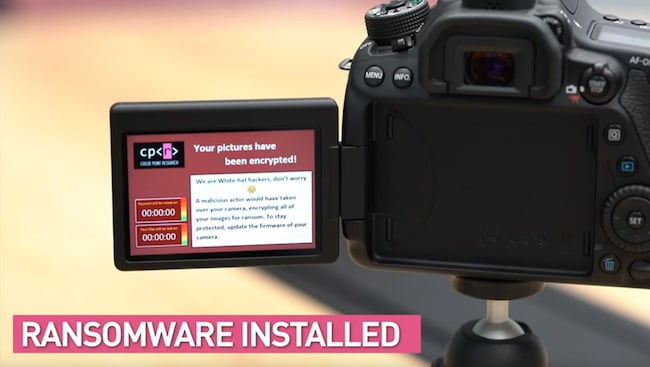
Replay: And you thought you had enough to worry about. An Israeli security research firm has published a post where they detail how they installed ransomware on a Canon EOS 80D.
The security researchers in question are called Check Point Research and they started off this ransomware project by asking a very simple question: “Could hackers take over our cameras, the guardians of our precious moments, and infect them with ransomware?”
The answer: yes.
It’s not an easy ‘yes’ but it is a ‘yes’. Essentially a hacker on the same WiFi network or who has already infected a connected PC can exploit vulnerabilities in the Picture Transfer Protocol (PTP) to effectively take over the camera.
As CPR points out, from an attacker’s perspective, the PTP layer looks like a great target: PTP is an unauthenticated protocol that supports dozens of different complex commands; vulnerability in PTP can be equally exploited over USB and over WiFi; and the WiFi support makes cameras more accessible to nearby attackers.
Ransomware was the first thing the researchers thought to try — send bitcoins or never see your pictures or use your camera again! — but there are probably several other nefarious uses a hacker could put a hacked camera to. And it’s not a case of non-Canon owners feeling smug either. Having uncovered the vulnerability, CPR informed Canon who issued a patch, and it has been only after its publication last week that the company has now gone public with the story.
You can read more about the hack in fairly excruciating technical detail here Say Cheese: Ransomware-ing a DSLR Camera or watch the video below. But we leave you with these comforting words.
“During our research we found multiple critical vulnerabilities in the Picture Transfer Protocol as implemented by Canon. Although the tested implementation contains many proprietary commands, the protocol is standardized, and is embedded in other cameras. Based on our results, we believe that similar vulnerabilities can be found in the PTP implementations of other vendors as well.”
Tags: Production


Comments